Look at me, Mom I’m a bot!
This Pearl script is impressive. It was uploaded to a cowrie instance. The script has a connection back to the attackers via IRC using 2[.]57[.]122[.]80. This IP address maps back to a hosted datacenter [https://]dmzhost[.]co. This looks like a purchasable cloud instance the malicious actor is using to run the IRC.
I made attempts to gain access to the IRC channel; however, I was unsuccessful. I then turned to some general open information about the IP while I waited for a full Nmap of all ports of the IP in question. This IP has had little history of malicious activity. Checking over my normal stops of urlscan.io, graynoise.io, iplocation.io, and otx.alienvault.com I found only a few hits.
Graynoise:

Alienvault:

The Alienvalt search even returned the same file hash that landed on my honeypot. Interesting however that the first seen date in many of the reports was from the beginning of October. I was hopeful that the host would still be up and have some interesting services I could poke at. Unfortunately, the Nmap scan came back un-eventful and my further poking did not produce any interesting events.
nmap:
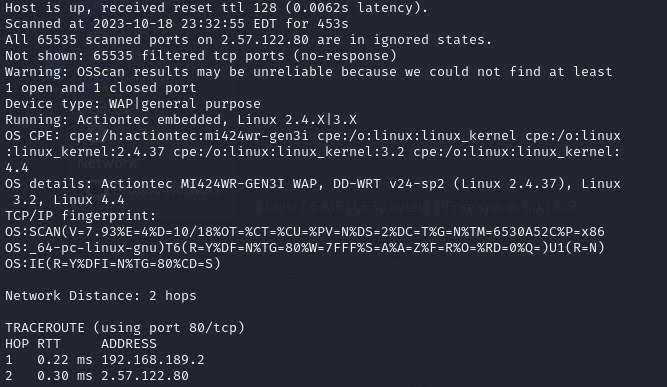
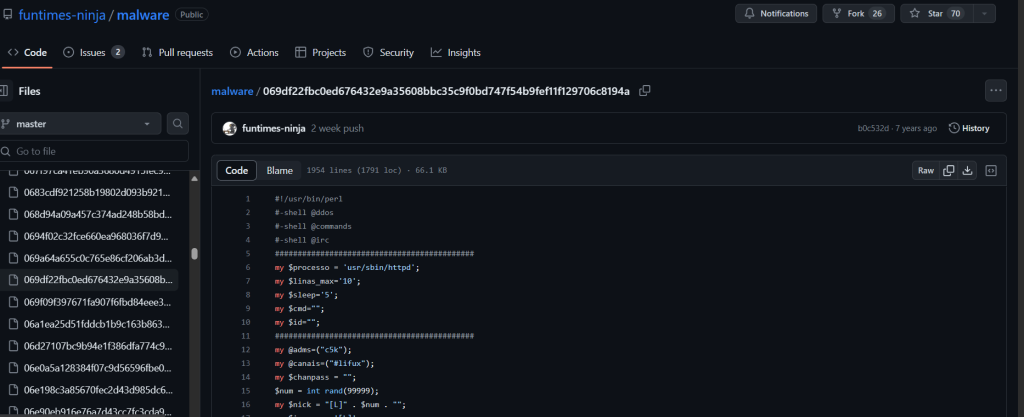
I would suspect that whatever this was at, this IP has now moved on or is turned down. The script it dropped was lengthy and packed full of fun. See the end of this post for your own review of the code that I uploaded to my GitHub. However, as we have seen in recent uploads to the honeypot, it is nothing new. Some quick searches on the web for elements from this script, and I was able to find it on a GitHub page published 7 years ago.
GitHub:
Defender Notes:
This script made its way into the system via an upload via an insecure and public SSH server. Don’t do that. This script will make a fair amount of noise once it is in using some well-known tools. It should be easily detectable with a well-tuned SIEM. It does have scripts with it to clear logs so if you not shipping logs to a SIEM you may not catch this activity.
Malicious Script: